AWS ElasticSearch — Bastion server for accessing Kibana.
There are times when access to kibana is necessary for debugging and monitoring. One finds it difficult to access kibana if the Elasticsearch server is placed inside the private subnet of a VPC. The private subnet does not allow any kind of communication to the server via public networks thereby denying access to kibana and other elastic search applications. There are two methods by which the above issue can be resolved —
Creating an Nginx reverse proxy server in the same VPC public subnet

More details on this process can be found in the upcoming blog.
Creating a Bastion server in the same VPC public subnet
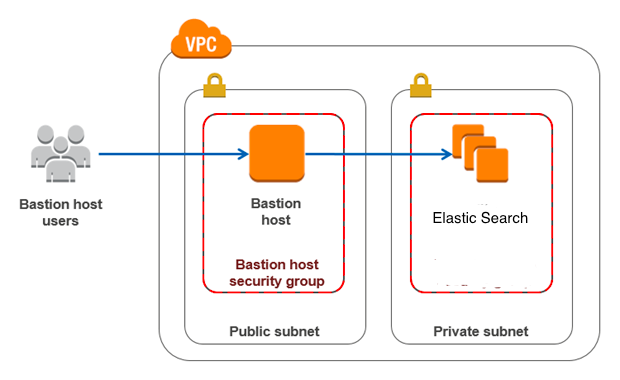
We will be using the Bastion Host in this post.
What is a Bastion Host?
A bastion host is a server whose purpose is to provide access to a private network from an external network such as the Internet. Because of its exposure to potential attacks, a bastion host must minimize the chances of penetration.
What is SSH Tunneling? or What is Port Forwarding vis SSH?
SSH tunneling or port forwarding is a mechanism in SSH for connecting application ports from the client machine to the server machine or vice versa. For most IT applications, it is used for adding encryption to legacy applications, going through firewalls, and for opening backdoors into the internal network from their local network or corporate network machines.
Port forwarding via SSH (SSH tunneling) creates a secure connection between a local computer and a remote machine through which services can be relayed. Because the connection is encrypted, SSH tunneling is useful for transmitting information that uses an unencrypted protocol.
Setup AWS bastion Host in a public subnet
A bastion host is a Linux server on the public subnet. We will first create an EC2 (t2.micro) server. The security group will allow all inbound connection to Port 22 (ssh port) only. However, the outbound could be anything- you’re free to restrict.
Lets quickly create an EC2 Linux bastion —



The Linux instance is created and now available to be used.
Lets quickly look at the ElasticSearch server-

SSH Tunneling —
The idea here is to connect to the Linux bastion server via SSH and then use local forward to the Elastic Search in the private VPC. Since both the servers (Bastion and Elastic Search) are in the same VPC they can communicate via private address. Next, we map the ssh tunnel to the Localhost of the user system. This result would be creating a backdoor to kibana mapped on the localhost secured with a private key and additional user-designed security.
The Fun part — it’s just 6 lines of configuration file
open the config file of ssh to add the changes.
sudo nano ~/.ssh/config , you could also use vim or any other editor
Host Bastion-tunnel
HostName 52.xx.xxx.xx
User ubuntu
IdentitiesOnly yes
IdentityFile ~/Downloads/ashu-personal.pem
LocalForward 9200 vpc-medium-elastic-itabcropnjgu2cio2565ctemvy.ap-southeast-1.es.amazonaws.com:80Let's understand the config file.
Host Bastion-tunnel
# The name of SSH tunnel could be your own choice HostName 52.xx.xxx.xx
# the public ip address of the Bastion Server User ubuntu
# User name is "ubuntu" as we are using the ubuntu server IdentitiesOnly yes
# Enabling the authorisation via ssh private keyfile IdentityFile ~/Downloads/ashu-personal.pem
# Location of the identity file LocalForward 9200 vpc-medium-elastic-itabcropnjgu2cio2565ctemvy.ap-southeast-1.es.amazonaws.com:80# localForward 9200 (port to be operated on the localsystem)
# vpc adddress without the https
# 80 or 443 for HTTP or HTTPS
Voila!

